Nowadays, software development relies heavily on a myriad of third-party libraries, each crafted by different developers with unique coding styles and preferences. However, this vast pool of resources often comes with a significant challenge: the lack of transparency. Closed-source software makes code auditing a daunting task, leaving users in the dark about what exactly they are running on their systems. It's akin to consuming food without knowing its ingredients – a potentially risky venture.
Deepbits specializes in unraveling the intricate web of third-party libraries, offering a solution to the elusive nature of compiled software. Our approach begins with the disassembly of binary files, utilizing our in-house fast and accurate disassembler to capture function features. By identifying potential third-party libraries through these function features, we employ a deep neural network-based graph matching techniques to refine our results, meticulously eliminating false positives. To take it a step further, we pinpoint vulnerable code using the power of pseudocode diffing. By elevating assembly code to intermediate representations (IRs) and constructing inter-procedural program dependency graphs (IPDG), we delve deep into the codebase, allowing us to identify vulnerabilities at the token level in decompiled code.
To demonstrate the practical application of our techniques, we conducted patch detection on Zoom, a popular closed-source video-conferencing application. Our results were compared with those from industry-standard tools such as BinDiff 1 and Diaphora 2. This comparison illustrates how Deepbits can play a pivotal role in auditing unknown binary files. Our analysis spanned both the Linux version (v5.9.6.2225) and Windows version (v5.9.7.3931) of Zoom.
Upon analyzing the Zoom binary files, we identified five open-source libraries and their respective versions: OpenSSL 1.1.1k, SQLite 3.33.0, resiprocate 1.11, libjpeg-turbo 2.0.4, and FFmpeg 4.2.3. To validate the presence of vulnerabilities in Zoom binary files, we performed diffing between the Zoom binary files and the corresponding binary of the latest version. The table below lists the evaluation results. In total, we were able to identify thirteen vulnerabilities across these five libraries in both the Linux and Windows versions of Zoom. Notably, our approach precisely pinpointed eight of these vulnerabilities at the token level, meaning the tokens related to the patches were precisely identified. For the remaining five vulnerabilities, we were still able to locate vulnerable functions.
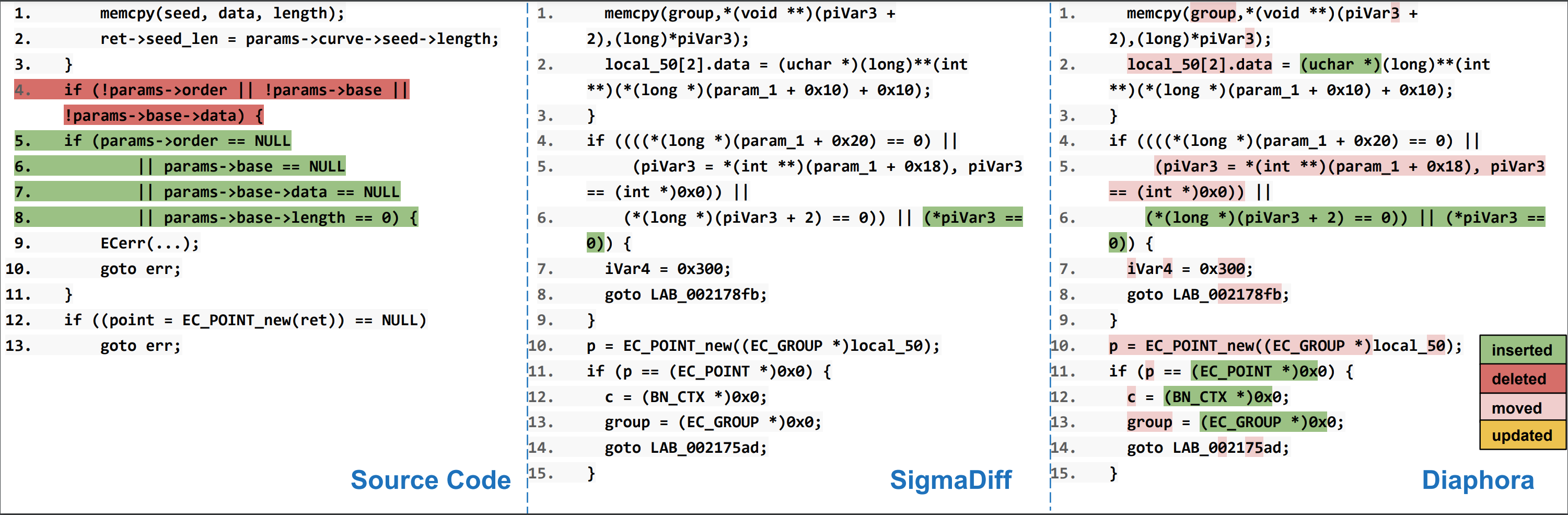
Take CVE-2021-3712 for example, the vulnerable function EC_GROUP_new_from_ecparameters attempts to read the first byte in the buffer without first checking the buffer size: EC_GROUP_set_point_conversion_form(ret, (point_conversion_form_t) (params->base->data[0] & ~0x01)); This vulnerability was fixed by this patch, which added a check to ensure there's at least one byte in params->base before trying to read it. To confirm the presence of this vulnerability in the Zoom binary files, we compared the corresponding file with the latest version (1.1.1n, at the time of this evaluation) of OpenSSL. The figure below illustrates the diffing results of the source code, our approach, and Diaphora. It is evident that our approach pinpoints the additional condition added by the patch, making it much easier to confirm the presence of patches. In contrast, the result from Diaphora shows several moved and inserted statements, leaving ambiguity about whether the patch has been applied or not.
- More details of the diffing technique mentioned in this blog can be found in this paper. The paper will be presented at NDSS 2024.
| Library | Version | CVEs | Function-lvl | Token-lvl | ||||
|---|---|---|---|---|---|---|---|---|
| De | Di | Bi | De | Di | Bi | |||
| OpenSSL | 1.1.1k | CVE-2023-0464 | ✓ | ✓ | ✓ | |||
| CVE-2023-0215 | ✓ | |||||||
| CVE-2022-4450 | ✓ | ✓ | ✓ | |||||
| CVE-2022-0778 | ✓ | ✓ | ✓ | ✓ | ✓ | |||
| CVE-2021-3712 | ✓ | ✓ | ✓ | |||||
| CVE-2021-3711 | ✓ | ✓ | ||||||
| SQLite | 3.33.0 | CVE-2022-35737 | ✓ | |||||
| CVE-2021-20227 | ✓ | |||||||
| resiprocate | 1.11 | CVE-2021-3672 | ✓ | ✓ | ||||
| CVE-2017-9454 | ✓ | ✓ | ||||||
| libjpeg-turbo | 2.0.4 | CVE-2020-13790 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| FFmpeg | 4.2.3 | CVE-2021-38291 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| CVE-2020-22037 | ✓ | ✓ | ✓ | ✓ |