🔍 Third-Party Security
Assess & Manage
Third-Party Risk
Comprehensive security analysis for third-party software components and dependencies
🔍 Third-Party Security
Assess & Manage
Third-Party Risk
Comprehensive security analysis for third-party software components and dependencies
🚀 Start Free Trial
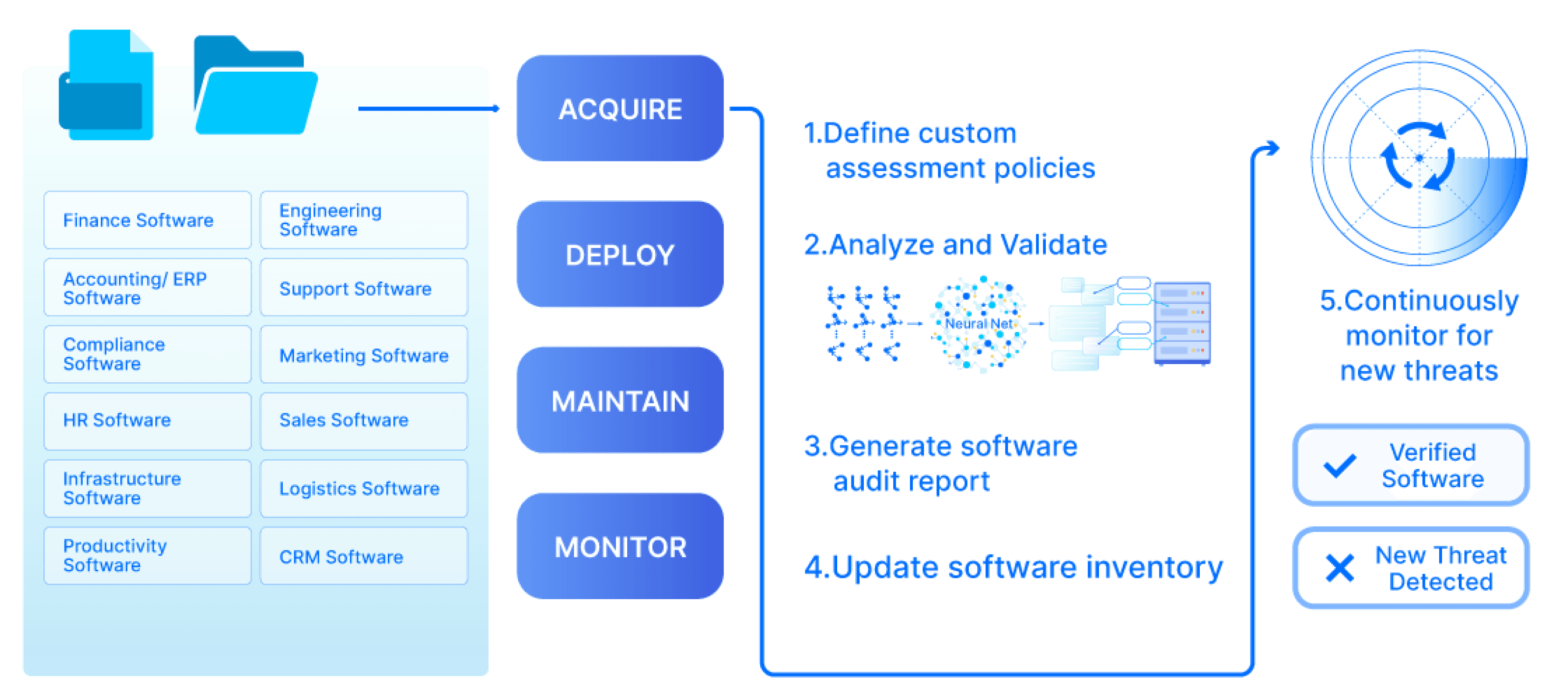
Automatically Analyze Software for Supply Chain Threats
Submit & Analyze
Swiftly assess software binaries, containers, open-source libraries, third-party software, and SBOMs for potential threats.
Uncover, Resolve & Respond
Unearth high-risk software, resolve risks embedded in intricate software dependencies, isolate threats upon their occurrence.
Verify, Approve & Deploy
Thoroughly verify security compliance, authorize based on custom criteria, and safely launch into production environments.
Continuously Monitor
Constantly spot, examine, and address emerging risks introduced across the software lifecycle
Solution Insights
How Binary Code AI Changes Malware Defenses?
Read Article
Unveiling Third-Party Libraries (and Their Vulnerabilities) in Closed-Source Applications
Read Article
Building SBOMs for COTS Android Apps
Read Article
A Fast and Accurate Disassembler based on Deep Learning
Read Article
Discovering Known Vulnerabilities in IoT Devices via Code Search
Read Article
How Do You Upgrade OpenSSL in Your Software Stack? — SBOM and OBOM assisted software upgrade
Read Article
Upload and get free risk assessment report right now!
Get instant vulnerability analysis and risk assessment for your software components
Binary File
Upload
X86 ELF, X64 ELF, ARMv8 ELF
Android APK file
Java archive file, .war, .ear, .par
.egg
Rust binary
Go binary
Metadata File
Upload
composer.lock
pom.xml, gradle.lockfile
yarn.lock, package-lock.json, package.json, pnpm-lock.yaml
poetry.lock, Pipfile.lock, requirements.txt
Gemfile.lock, .gemspec
Cargo.lock
go.sum, go.mod